- Published on
Cryptography
Cryptography
History of Cryptography
Cryptography is a method of keeping information secret that has been around for more than 2500 years. It has always been a competition between those who create codes and those who break them. In the past, people used things like paper and ink, cryptographic engines, telegrams, and radio to do cryptography. Today, computers and digital communication are used for modern cryptography.
Terminology
- Plaintext: the original message
- Ciphertext: the transformed message
- Key: the secret used in the transformation
- Encryption: the process of transforming plaintext into ciphertext
- Decryption: the process of transforming ciphertext back into plaintext
- Cipher: the algorithm used for encryption/decryption
Security Goals (CIA)
- Confidentiality: Only authorized individuals may access the information.
- Integrity: Only authorized parties can change the information using authorized methods.
- Availability: Authorized individuals can access the information.
Security Principles
- Hiding information is not a reliable way to keep it secure.
- Assume the person trying to break in knows how your security system works, except for your password or secret key.
Secure Communication
Secure communication is a way of protecting data from unauthorized access. It involves encryption and other measures to ensure data is securely transmitted between two or more parties. Encryption is scrambling data so that it can only be read by the intended recipient.
Approaches to Secure Communication
- Steganography:
covered writingthat hides the existence of a message. It depends on the secrecy of the method used. - Cryptography:
hidden writingthat hides the meaning of a message. It depends on the secrecy of a short key, not the method used.
Cryptography, Cryptanalysis, Cryptology
- Cryptography is the process of creating algorithms and protocols that are used for security purposes. It is often used interchangeably with cryptology.
- Cryptanalysis is the process of breaking cryptography.
- Cryptology refers to both cryptography and cryptanalysis, but this term is becoming less common.
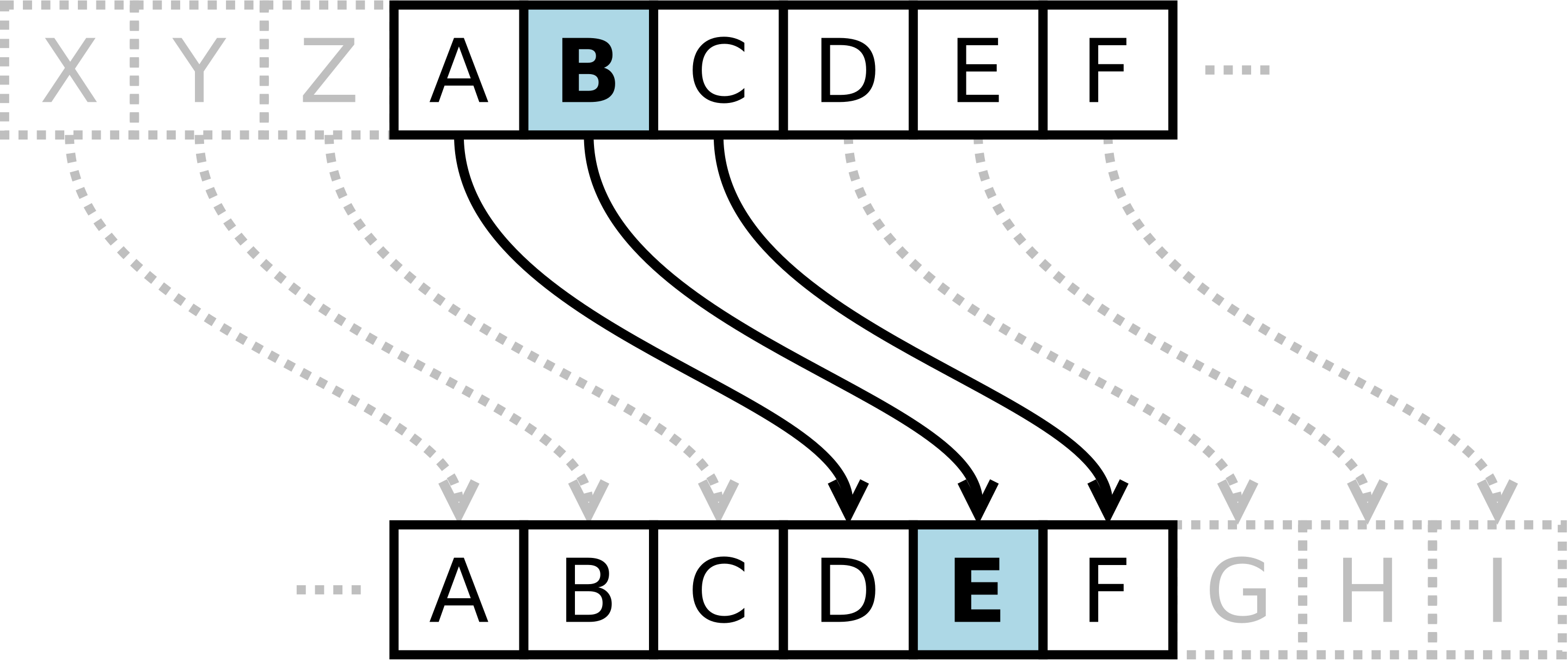
Shift Cipher(Caesar’s cipher)
- Each letter in the plaintext is replaced by a letter K positions ahead of it in the alphabet.
- An attacker can find K by trying every possible key since there are only 25 possible keys or fewer(key 0 return plaintext).
- Once K is found, encryption is very easy.
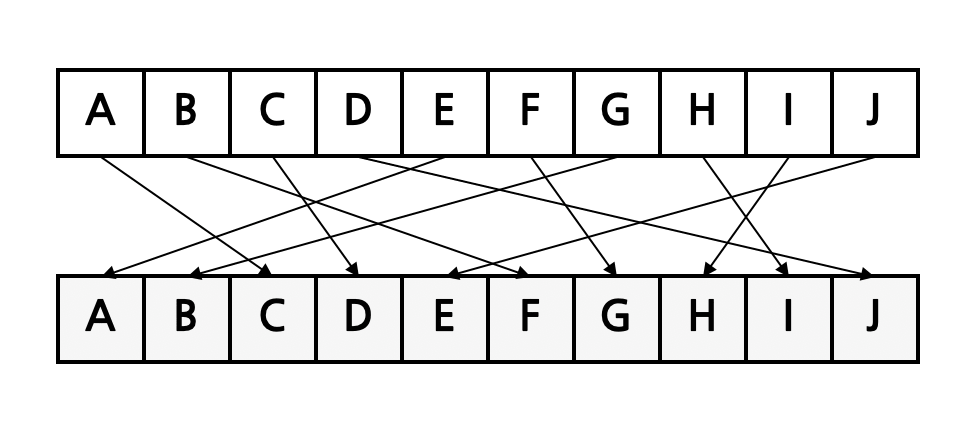
Substitution Cipher
- Each letter X in the plaintext P is replaced with Y.
- They dominated the art of secret writing throughout the first millennium A.D.
- They were thought to be unbreakable by many back then.
- Substitution ciphers are vulnerable to frequency analysis attacks. Each language has certain features such as the frequency of letters or groups of two or more letters.
One-Time Pad (OTP)
- OTP improves substitution cipher by using different keys to encrypt letters in different positions.
- The key should be a random string that is at least as long as the plaintext, according to Shannon's theorem.
- Shannon's theory states that the ciphertext should not reveal any information about the plaintext.
- Encryption is similar to the shift cipher.
- OTP was invented by Vernam in the 1920s.
- Never use the same key in OTP more than once.
Stream Cipher
- The One-Time Pad encryption method uses a random key that is at least as long as the message being encrypted.
- Stream ciphers use a Pseudo Random Number Generator (PRNG) to create a sequence of numbers that appear random.
- Stream ciphers are usually fast.
- RC4 is a proprietary stream cipher owned by RSA, which became public in 1994.
- SSL/TLS uses RC4. SSLv3 does not have any major known vulnerabilities.
- If the same stream is used more than once, it becomes easy to break.
- These vulnerabilities are basic and still exist regardless of the strength of the PRNG.
Pseudo Random Number Generator (PRNG)
- A PRNG is a tool used for cryptography and simulation.
- When using the same seed, a PRNG will always give the same output stream.
- For a PRNG to be cryptographically secure, it needs to have unpredictable sequences.
- PRNGs are also useful for generating temporary keys and other similar tasks.
Adversarial Models for Ciphers
- The attacker is supposed to know the language of the original message and the type of encryption used.
- Ciphertext-only attack: The attacker can only see some encrypted messages.
- Known-plaintext attack: The attacker has seen some pairs of encrypted and decrypted messages.
- Chosen-plaintext attack: The attacker can choose some messages and see the corresponding encrypted messages.
- Chosen-ciphertext attack: The attacker can choose some encrypted messages and see the corresponding decrypted messages.
Data Encryption Standard (DES)
- DES was designed by IBM with modifications proposed by the National Security Agency.
- From 1977 to 2001, it was a US national standard.
- It uses a block size of 64 bits and a key size of 56 bits.
- It has 16 rounds and was mostly designed for hardware implementations.
- However, it is now considered insecure and vulnerable to brute-force attacks.
Data Integrity and Source Authentication
Encryption does not fully protect data from being changed by someone else. To make sure the data gets to its destination without being changed and to make sure it comes from a known source, we need something else.
Cryptographic Hash Function
A hash function maps a message of arbitrary length to an m-bit output.
Since a hash function is a many-to-one function, collisions can occur.
Hash functions are used for the following examples:
- Software integrity
- Timestamping
- Message authentication
- One-time passwords
- Digital signatures
Well-known hash functions
- MD5 - produces a 128-bit output. It has been completely broken by researchers in terms of collision resistance.
- SHA1 - produces a 160-bit output. No collisions have been found yet, but there is a method to find collisions in less than 2^80 attempts. It is considered insecure for collision resistance.
- SHA2 (SHA-224, SHA-256, SHA-384, SHA-512) - produces 224, 256, 384, and 512 bits output, respectively.
- Hash outputs should generally be
twicethe key length of block ciphers due to the birthday attack.
Limitations of Using Hash Functions for Authentication:
- Anyone can calculate the hash of a message, since the hash function is public.
- It is not always possible to have a secure channel.
To fix these issues, you can:
- Use multiple hash functions.
- Select a hash function with a key.
Encryption and Authentication (3 Ways)
- Authenticate-then-encrypt (AtE): This method is used in
SSL. However, AtE may not always be secure because the first step is decryption, which can reveal whether the decryption was successful or not. - Encrypt-then-authenticate (EtA): This method is used in
IPSec. Encryption alone may not be enough to ensure privacy. EtA is a secure option. - Encrypt-and-authenticate (E&A): This method is used in
SSH. However, the MAC method does not guarantee confidentiality.
RSA Algorithm
The most common public-key algorithm is called the RSA method, named after its inventors (Rivest, Shamir, Adleman). In this algorithm, the private key is a pair of numbers (N, d), and the public key is a pair of numbers (N, e). It should be noted that N is common to both the private and public keys.