- Published on
Firewall Security
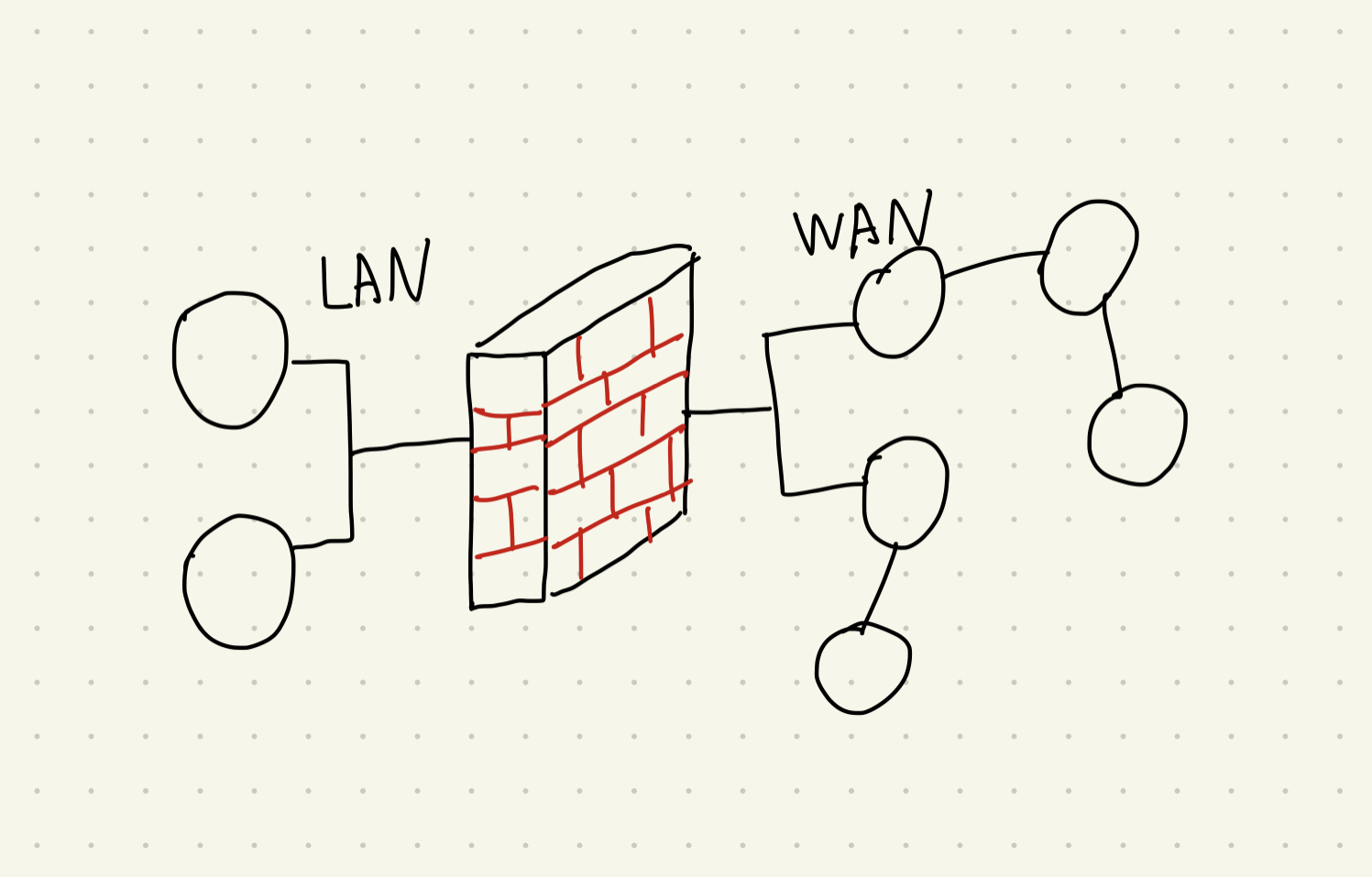 A firewall is a network security device, either hardware or software-based, that monitors all incoming and outgoing traffic based on a defined set of security rules. It establishes a barrier between secured internal networks and untrusted outside networks, such as the internet. The basic security functions are
A firewall is a network security device, either hardware or software-based, that monitors all incoming and outgoing traffic based on a defined set of security rules. It establishes a barrier between secured internal networks and untrusted outside networks, such as the internet. The basic security functions are packet filtering and application proxy
The Need for Firewalls
- Before firewalls, network security was maintained using Access Control Lists (ACLs) that were located on routers. ACLs are rules that determine whether network access should be allowed or denied to specific IP addresses. However, ACLs cannot determine the type of packet being blocked, nor can they keep threats out of the network on their own. This is why firewalls were created.
- Organizations require access to the internet, but to keep their networks secure, they need a firewall to block unauthorized access.
Set of Security Rules
- Accept: Allows the traffic.
- Reject: Blocks the traffic and replies with an "unreachable error."
- Drop: Blocks the traffic with no reply.
Generations of Firewalls
1st Generation (Packet Filtering Firewall):
A packet-filtering firewall makes decisions based on each individual packet.
2nd Generation (Stateful Inspection Firewall):
A stateful inspection firewall can determine the connection state of a packet. It keeps track of the state of network connections traveling across it, such as TCP streams. Filtering decisions are not only based on defined rules but also on the packet's history in the state table.
3rd Generation (Application Layer Firewall):
An application layer firewall can inspect and filter packets on any OSI layer, up to the application layer. It has the ability to block specific content and recognize when certain applications and protocols are being misused.
Application layer firewalls are hosts that run proxy servers. A proxy firewall prevents the direct connection between either side of the firewall; each packet has to pass through the proxy. It can allow or block traffic based on predefined rules. It can also be used as a network address translator (NAT).
Next-Generation Firewalls (NGFW)
- NGFWs are being deployed to stop modern security breaches, such as advanced malware and application-layer attacks.
- NGFWs consist of deep packet inspection, application inspection, SSL/SSH inspection, and other functionalities that protect the network from these modern threats.
Firewall filtering
IP Addresses and Protocols:
Packet filters and stateful inspection firewalls use this type of filtering to limit access to specific services
Application protocol:
This type of filtering is used by a gateway that relays and monitors the exchange of information for specific application protocols.
User Identity:
This is for users who identify themselves with a secure authentication method.
Network Activity:
Manages access based on factors such as the time of the request, the frequency of requests, or other activity patterns.
Firewall Capabilities and Limitations
Capabilities:
- Establishes a single choke point
- Provides a location for monitoring security events
- Convenient platform for several internet functions
- Can serve as the platform for IPSec
Limitations:
- Cannot protect against attacks that bypass the firewall
- May not fully protect against internal threats
- Improperly secured wireless LAN can be accessed from outside the organization
- Laptops, PDAs, or portable storage devices may be infected outside the corporate network and then used internally
Network Traffic
Network traffic can be either outgoing or incoming. Firewalls maintain distinct sets of rules for both cases.
Outgoing Traffic:
Egress filtering inspects outgoing network traffic and prevents users on the internal network from accessing the outside network. For example, social networking sites can be blocked in schools. Mostly, outgoing traffic originating from the server itself is allowed to pass, but it's always better to set a rule on outgoing traffic to achieve more security and prevent unwanted communication.
Incoming traffic:
Ingress filtering is a way to protect a network from outside attacks by checking incoming traffic. This traffic is usually one of three types: TCP, UDP or ICMP. Each type has a source and destination address, and TCP and UDP also have port numbers. ICMP uses a different way to identify the purpose of a packet, by using type codes instead of port numbers. The firewall treats incoming traffic differently from other traffic.
Firewall Access Policies
To plan and use a firewall effectively, you need to make sure it lets through the right kind of traffic. This includes things like address ranges, protocols, applications, and content types. To make this happen, you should use your organization's security risk assessment and policy to create a list of the kinds of traffic you need to support. Then, you can break that list down into more detail to figure out how to filter everything using the right kind of firewall setup.
Firewall policy
- Default policy: The firewall has to have a default policy because it's hard to cover every rule. The default policy only says what to do (accept, reject, or drop). Here's an example: If the firewall doesn't have a rule for SSH connections to the server, it will follow the default policy. If the default policy is set to accept, any computer outside of your office can establish an SSH connection to the server. Setting the default policy to drop (or reject) is a good practice.
- User control: Controls access to data based on the user's role. This applies to users inside the firewall.
- Service control: Controls access based on the type of service offered by the host. This is based on network address, protocol, and port numbers.
- Direction control: Determines the direction of requests allowed through the firewall. It specifies whether traffic is "inbound" (to the firewall) or "outbound" (from the firewall).
Firewall Actions
- Accepted: Allowed to enter the network or host through the firewall.
- Denied: Not allowed to enter the other side of the firewall.
- Rejected: Similar to "Denied", but the source is informed about the decision through an ICMP packet.
Firewall Security Features
Advanced security features provided by certain firewalls:
- Logging
- VPN
- Authentication
- Shielding hosts within the network to prevent attackers from identifying them and using them as a base for prolonged attacks
- Data caching
- Filtering content deemed inappropriate
Types of Firewalls
1. Host-based Firewalls: Host-based firewalls are software applications or suites of applications installed on each network node. They control each incoming and outgoing packet. Host-based firewalls are needed because network firewalls cannot provide protection inside a trusted network. Host firewalls protect each host from attacks and unauthorized access.
2. Network-based Firewalls: Network firewalls function on the network level, filtering all incoming and outgoing traffic across the network. They protect the internal network by filtering the traffic using rules defined on the firewall. A network firewall might have two or more network interface cards (NICs). A network-based firewall is usually a dedicated system with proprietary software installed.
iptables
- Linux's built-in firewall
- iptables is the user-space program
- firewall in the kernel called Xtables
- iptables is commonly used to refer to both programs
- iptables [-t filter] -A INPUT <rule> -j <target>
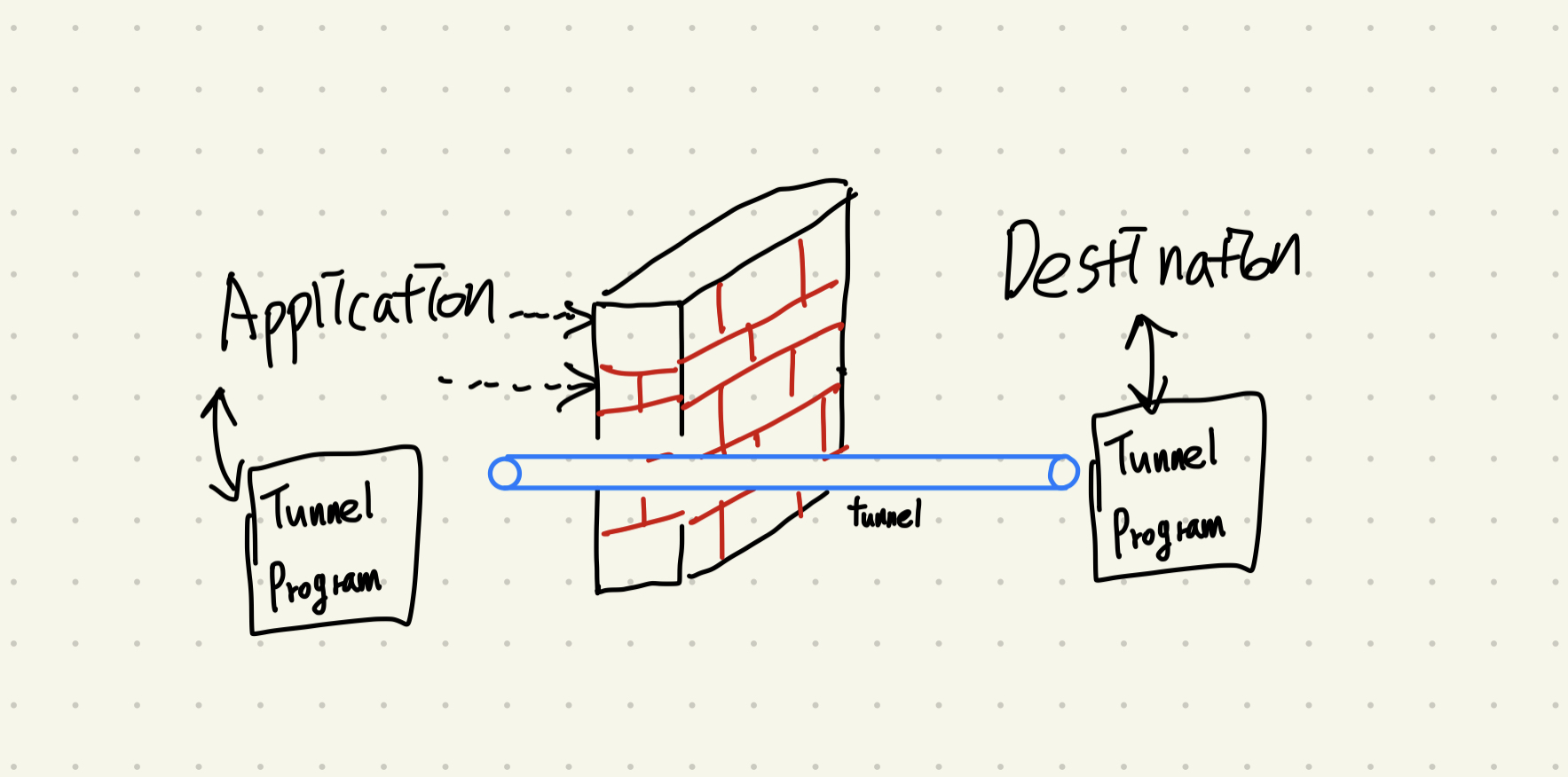
bypassing firewall
By using vulnerabilities and tunneling, it is possible to bypass a firewall.